I have recently been following Fon, a movement that aims at creating a worldwide WiFi network, with Bills, Linuses and Aliens sharing their broadband with others, some for free, others for profit – split with Fon. The basis of Fon is that you connect a Linksys WRT54Gx WiFi router running special firmware to your broadband internet connection. This firmware turns the router into a captive portal, which then allows you to control access to the internet.
During the last couple of weeks, there has been some noise at Fon about having finally achieved production of their own WiFi router – they call it La Fonera. The move may seem obvious, as right now, they are buying the Linksys routers at full reseller price, in turn reselling them heavily subsidized at $25 a piece $1, as I’ve just read a minute ago. What I still don’t get is the title of the recent post in Martin Varsavsky’s blog, ‘Fon, the Social Router’.
A few days ago, Fon announced the purchase of 1.000.000 (literally!) of these new routers from the taiwanese manufacturer Accton. This company already manufactures WiFi routers, amongst other devices, and so it’s perfectly plausible that they can manufacture a customized router for Fon.
The main reason for manufacturing anything in China or Taiwan is the labour costs are extremely low. The electronics aren’t cheaper over there, and as a matter of fact, most of the core components are sold by western companies, such as Broadcom, Intel and Atmel. Labor conditions in chinese plants vary, from outright slavery to pretty good, but even then, one thing is a fact: they work all year round, including all weekends, only having ten days off for the Chinese New Year.
Reading Accton’s site, it appears that they treat their workers very well, and I applaud that. But this also means that they cannot produce as cheaply as the sweatshop-style manufacturers. A WiFi router with the horsepower required to run Fon’s platform is not cheap – let’s estimate roughly $22 per unit, for a purchase of 1 million units. If this estimate is correct, Fon would have blown on these routers a tad more than the entire funding they got from Skype, Sequoia, Index and Google.
If they were to give away the routers, to recoup this investment Fon would have to sell approximately 11 million 24-hour access packages, at $2 each. That is assuming Fon takes 100% of the money – with the Bill model, they would only get 50% of the income, as it is shared with the person providing the broadband and maintaining the hotspot. If they were to sell the routers at cost, they’d still have a huge logistics nightmare in their hands. Failure rates in mass-produced electronics range between 1% and 3%, meaning they could have up to 30.000 returns, costing them $1.32 million in hardware, plus logistics and other costs. One thing is to be a promoter of social WiFi – another is to turn into a hardware manufacturer – be it by ODM contracts, or by making the devices yourself.
So, I leave some open questions: has Fon chosen a company that respects human rights, treats its workers with dignity, but won’t give them a good deal as they could have gotten somewhere else, thus affecting their ROI expectations? Does investing in 1 million routers make economic sense with their current business model?
 Yes. It wanted us to go up a dirt path that only horses (and fit ones at that) can manage. Take a close look at the full-resolution picture, and judge by yourself.
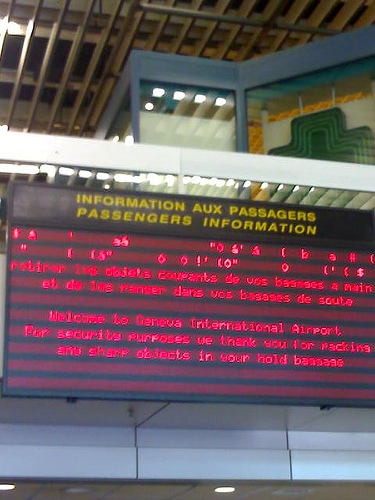
Yes. It wanted us to go up a dirt path that only horses (and fit ones at that) can manage. Take a close look at the full-resolution picture, and judge by yourself.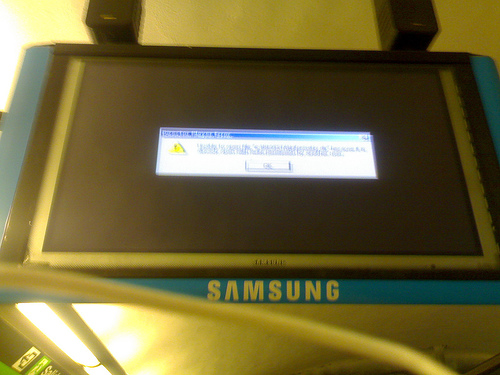 HUDs are public displays, screens and panels which are caught showing something they shouldn’t be, by fault or by hack. There is a classic roadside HUD
HUDs are public displays, screens and panels which are caught showing something they shouldn’t be, by fault or by hack. There is a classic roadside HUD