This was seen on a Boeing 767 while en route from Las Vegas to Atlanta, the flight being operated by Delta. Apparently, many people were having problems with their purchased movies, and so the crew decided to reset the system, provoking a nicely familiar sight.
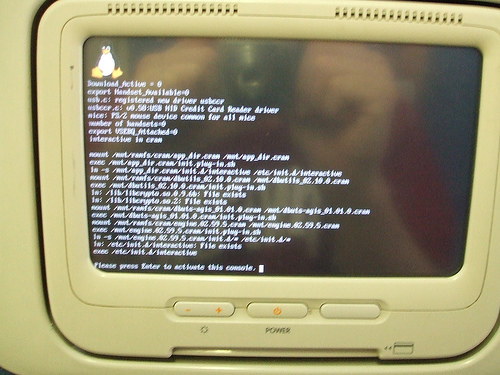
Now we could all start making jokes about nmapping the plane, or trying to run Asterisk off a USB drive plugged into the management console, which by the way was accessible to anyone who wandered to the toilet and happened to look left. It had a nice big “Reset all” button too, two USB ports, and a gigabit etherenet RJ45. I just hope they don’t run a kernel with some remote_crash_plane() buffer overflow exploit…



