Last Saturday, while reading through my feeds, I noticed this post on TechCrunch by Duncan Riley, where he tells the story of an attempt by scammers to get his Skype credentials (and wonders why they’d want to do such a thing), much in the same way we’re accustomed to receive emails from PayPal, eBay, and almost any bank on earth. These emails claim there is a problem with your account, and you should ‘confirm your details’ in order to stop said account from being suspended. This will of course do nothing other than give your credentials to these criminals for unhealthy purposes.
Today, a friend that I had not chatted with in some time comes online, and sends me this: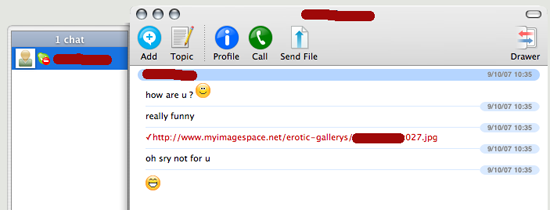
My first thought has been “Uhm, why would Mike send me something like this?”. He’s not prone to even send smilies, always very short and to the point. I go to ask him about it, but I then notice he is in do-not-disturb mode, so I cannot even warn him about the now-obvious scam! It seems that phishers and other scum are realizing people fall for email traps less and less, and are attacking other more trustworthy systems. In this case, the attacker is sending a screensaver, most likely loaded with a trojan. Beware of -any- communication, even from friends, that is unusual in timing, behavior or content. Also, beware about being asked for your IM details, and use strong passwords.